OCI healthchecks on AWS WAF protected resources
To check the health of your (public) webservices OCI has a nice health check feature. An AWS project has some resources that are customer facing and need to be checked. An initial setup is really self explaining, simply enter the endpoint and one or more vantage points from where the alive checks are made.
But… It did not work as expected, all checks failed with an 403 Forbidden although the resources are publically available. A check against a simple “hello world” nginx was successful. Checking the AWS site again, I noticed that the resources are protected by AWS Application Firewall with activated Bot-Control and it seems that WAF is protecting the application from the health check. To accept these requests, you can write a rule, that allows access from OCI health checks. In the AWS WAF console got to “Web ACLs” and click the “Rules” tab. Click “Add rules” and choose “Add my own rules and rule groups”. Use the json rule editor and paste this json:
{
"Name": "Allow_OCI_Health_Checks",
"Priority": 0,
"Statement": {
"ByteMatchStatement": {
"SearchString": "SoMeS3cretK3y",
"FieldToMatch": {
"SingleHeader": {
"Name": "x-bypass-secret"
}
},
"TextTransformations": [
{
"Priority": 0,
"Type": "NONE"
}
],
"PositionalConstraint": "EXACTLY"
}
},
"Action": {
"Allow": {}
},
"VisibilityConfig": {
"SampledRequestsEnabled": true,
"CloudWatchMetricsEnabled": true,
"MetricName": "Allow_OCI_Health_Checks"
}
}
We now created a rule, that allows access if an incoming request has the header x-bypass-secret with the value SoMeS3cretK3y.
Use this header in the health check.
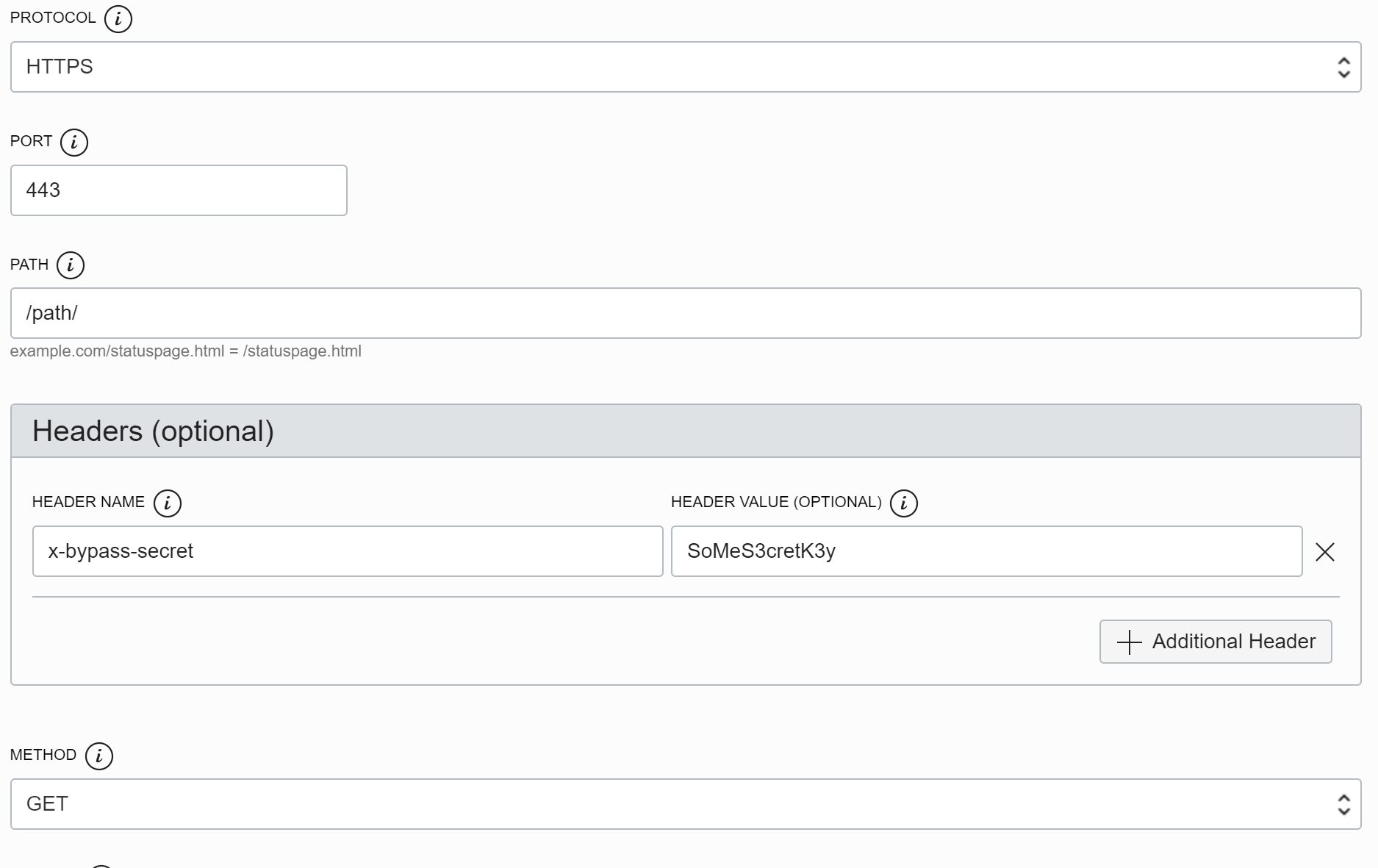
Now the check should work as expected from all vantage points!